ちょっとやりたいことあってAWSとIPSec張りたいなと。
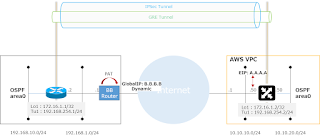
構成はこんな。
OSPFは別にいらないんだけど,折角なんでダイナミックルーティングをまわしてみる。
簡単にいけるかなーとも思ったけどかなりハマった。双方NAT配下で家のほうはさらにグローバルはDHCP割当で変わるわPATだからNAT-Tやらなきゃだとか,まーいろいろ気にするポイントがあった。
けど,無事につながりました。
大きくハマった点は以下2つ。
・CiscoのIPSec用ACLでgre指定だとNG。ip 指定で解消。
・Vyosのremote-idでCiscoの実IPを入れてあげる。
Vyosはわかるんだが,CiscoのACLはなんでだ。わからん・・・。
VTIとかでやればACL不要だからいいのかと思ったが,これはこれでハマったので又今度。
Try&Errorをひたすら試すはめになりました。
いい勉強させていただきました。
| ■ Cisco 抜粋 ! crypto isakmp policy 5 encr aes 256 hash sha256 authentication pre-share group 14 lifetime 3600 crypto isakmp key aws address A.A.A.A 255.255.255.255 crypto isakmp keepalive 30 30 ! ! crypto ipsec transform-set IPSEC esp-aes 256 esp-sha256-hmac mode tunnel ! ! crypto map GRE_IPSEC 10 ipsec-isakmp set peer A.A.A.A set transform-set IPSEC set pfs group14 match address AWS_GRE ! ! ! ! interface Loopback1 ip address 172.16.1.1 255.255.255.255 ! interface Tunnel1 ip address 192.168.254.1 255.255.255.0 ip mtu 1400 ip tcp adjust-mss 1360 ip ospf network broadcast ip ospf hello-interval 5 keepalive 5 3 tunnel source Loopback1 tunnel destination 172.16.1.2 ! interface Vlan100 ip address 192.168.1.2 255.255.255.0 ip virtual-reassembly in crypto map GRE_IPSEC ! ! ! router ospf 1 network 192.168.10.0 0.0.0.255 area 0 network 192.168.254.0 0.0.0.255 area 0 ! ! ip access-list extended AWS_GRE ! permit ip host 172.16.1.1 host 172.16.1.2 |
| ■ Vyos 抜粋 set interfaces loopback lo address ‘172.16.1.2/32’ set interfaces tunnel tun1 address ‘192.168.254.2/24’ set interfaces tunnel tun1 encapsulation ‘gre’ set interfaces tunnel tun1 ip ospf dead-interval ’20’ set interfaces tunnel tun1 ip ospf hello-interval ‘5’ set interfaces tunnel tun1 ip ospf priority ‘1’ set interfaces tunnel tun1 ip ospf retransmit-interval ‘5’ set interfaces tunnel tun1 ip ospf transmit-delay ‘1’ set interfaces tunnel tun1 local-ip ‘172.16.1.2’ set interfaces tunnel tun1 mtu ‘1400’ set interfaces tunnel tun1 multicast ‘enable’ set interfaces tunnel tun1 remote-ip ‘172.16.1.1’ set protocols ospf area 0 network ‘192.168.254.0/24’ set protocols ospf area 0 network ‘10.10.20.0/24′ set protocols ospf log-adjacency-changes ‘detail’ set protocols static route 0.0.0.0/0 next-hop 10.10.10.1 distance ‘1’ —- set vpn ipsec esp-group ESP_AWS compression ‘disable’ set vpn ipsec esp-group ESP_AWS lifetime ‘3600’ set vpn ipsec esp-group ESP_AWS mode ‘tunnel’ set vpn ipsec esp-group ESP_AWS pfs ‘enable’ set vpn ipsec esp-group ESP_AWS proposal 1 encryption ‘aes256’ set vpn ipsec esp-group ESP_AWS proposal 1 hash ‘sha256’ set vpn ipsec ike-group IKE_AWS dead-peer-detection action ‘hold’ set vpn ipsec ike-group IKE_AWS dead-peer-detection interval ’30’ set vpn ipsec ike-group IKE_AWS dead-peer-detection timeout ‘120’ set vpn ipsec ike-group IKE_AWS lifetime ‘3600’ set vpn ipsec ike-group IKE_AWS proposal 1 dh-group ’14’ set vpn ipsec ike-group IKE_AWS proposal 1 encryption ‘aes256’ set vpn ipsec ike-group IKE_AWS proposal 1 hash ‘sha256’ set vpn ipsec ipsec-interfaces interface ‘eth0’ set vpn ipsec logging log-modes ‘all’ set vpn ipsec nat-traversal ‘enable’ set vpn ipsec site-to-site peer 0.0.0.0 authentication mode ‘pre-shared-secret’ set vpn ipsec site-to-site peer 0.0.0.0 authentication pre-shared-secret ‘aws’ set vpn ipsec site-to-site peer 0.0.0.0 authentication remote-id ‘192.168.1.2’ set vpn ipsec site-to-site peer 0.0.0.0 connection-type ‘respond’ set vpn ipsec site-to-site peer 0.0.0.0 ike-group ‘IKE_AWS’ set vpn ipsec site-to-site peer 0.0.0.0 local-address ‘10.10.10.50’ set vpn ipsec site-to-site peer 0.0.0.0 tunnel 1 esp-group ‘ESP_AWS’ set vpn ipsec site-to-site peer 0.0.0.0 tunnel 1 local prefix ‘172.16.1.2/32’ set vpn ipsec site-to-site peer 0.0.0.0 tunnel 1 remote prefix ‘172.16.1.1/32’ |